
SSH server as SOCKS proxy
Securing internet access from public places using your SSH server.
This tutorial is a quick way to access internet from public places (hotels, airports) more securely using your own SSH server.
At first you need an ssh server accessible from the web. For example I am using a raspberry pi running in my home.
Then you need to configure your SSH server to listen on port accessible from any public internet spot. That means changing the default SSH port (22) to 80 or 443. So edit /etc/ssh/sshd_config file to include the line:
/etc/ssh/sshd_config
Port 443
...
We suppose now that you are in a public place with your mac or linux laptop, you know the ip of your home and you need to browse the web using your home's internet connection.
SSH manual
Here are the ssh client's options we are using:
~$ man ssh
-D [bind_address:]port
Specifies a local ''dynamic'' application-level port forwarding. This works by allocating a socket to listen to port on the local side, optionally bound to the specified bind_address. Whenever a connection is made to this port, the connection is forwarded over the secure channel, and the application protocol is then used to determine where to connect to from the remote machine. Currently the SOCKS4 and SOCKS5 protocols are supported, and ssh will act as a SOCKS server. Only root can forward privileged ports. Dynamic port forwardings can also be specified in the configuration file. IPv6 addresses can be specified by enclosing the address in square brackets. Only the superuser can forward privileged ports. By default, the local port is bound in accordance with the GatewayPorts setting. However, an explicit bind_address may be used to bind the connection to a specific address. The bind_address of ``localhost'' indicates that the listening port be bound for local use only, while an empty address or `*' indicates that the port should be available from all interfaces.
... and:
-C Requests compression of all data (including stdin, stdout, stderr, and data for forwarded X11, TCP and UNIX-domain connections). The compression algorithm is the same used by gzip(1), and the ``level'' can be controlled by the CompressionLevel option for protocol version 1. Compression is desirable on modem lines and other slow connections, but will only slow down things on fast networks. The default value can be set on a host-by-host basis in the configuration files; see the Compression option.
... and:
-N Do not execute a remote command. This is useful for just forwarding ports (protocol version 2 only).
Run port forwarding
From the laptop we are running:
~$ ssh -D 8080 -C -N <username>@<home ip> -p 443
We are entering the passord and we check that port forwarding is ok by running:
netstat -tunap | grep ssh:
tcp 0 0 127.0.0.1:8080 0.0.0.0:* LISTEN 17828/ssh
tcp6 0 0 ::1:8080 :::* LISTEN 17828/ssh
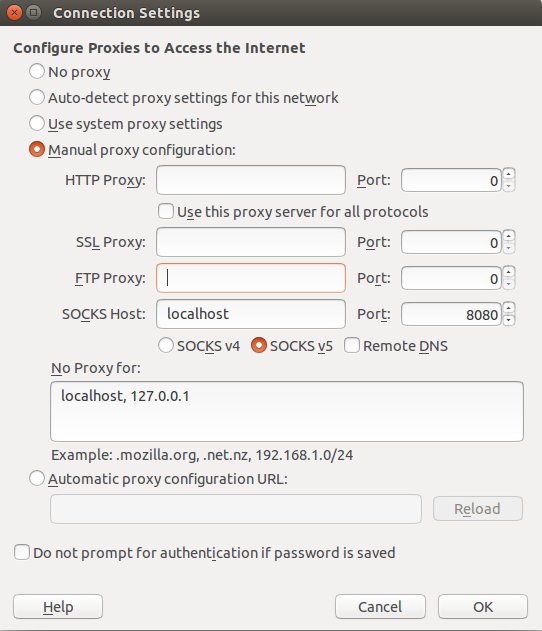
Config the browser
The last thing to do is to config our browser to use localhost:8080 as SOCKS proxy.
For example in firefox:
- Posted by Kostas Koutsogiannopoulos · June 26, 2016

